Difference between revisions of "Hacker Innovation and Consumer Artefacts"
Mikepinder (Talk | contribs) |
Mikepinder (Talk | contribs) |
||
| (7 intermediate revisions by the same user not shown) | |||
| Line 69: | Line 69: | ||
Both Computer Hobbyist and Enthusiast Programmer hacker types worked in collaborative innovation networks sharing knowledge via online technologies in to hack the TiVo box to enable service improvements such as circumventing country and regional blocks, installing larger hard drives, extracting videos to other PC’s and other TiVo boxes as well as file format decoding and encoding restriction removals. Essentially these hacks were carried out not to steal data, commit crime, destroy property or for personal financial gain, but were made to explore, unlock and share the unrealised potential functionality of design module configurations for personal benefit and as a passionate and pleasurable experience. | Both Computer Hobbyist and Enthusiast Programmer hacker types worked in collaborative innovation networks sharing knowledge via online technologies in to hack the TiVo box to enable service improvements such as circumventing country and regional blocks, installing larger hard drives, extracting videos to other PC’s and other TiVo boxes as well as file format decoding and encoding restriction removals. Essentially these hacks were carried out not to steal data, commit crime, destroy property or for personal financial gain, but were made to explore, unlock and share the unrealised potential functionality of design module configurations for personal benefit and as a passionate and pleasurable experience. | ||
| + | === Manufacturer and hacker artefact configuration states === | ||
| + | |||
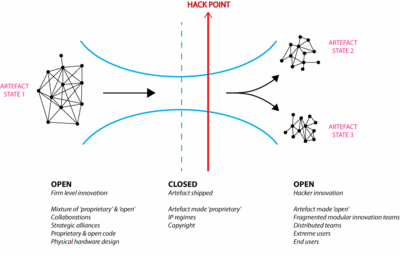
| + | The work undertaken by firm and hacker environments results in different artefact states as new module configurations are created, diffused and adopted by both parties (see conceptual diagram in Figure 1 below). Here artefacts pass from: an open to closed to open again configuration state. | ||
| + | |||
| + | # A manufacturer develops a new product based upon Open Source code with propriety software modules incorporated at shell layers. | ||
| + | # Proprietary and open code enters the marketplace locked and held within software and hardware configurations. | ||
| + | # Where access restrictions are found, hackers re-open the artefact to enable exploration of more optimised and feature rich design configuration states (at the ''hack point''). | ||
| + | # Hacker groups emerge through the use of ICT’s technologies sharing knowledge, learning and experience in order to optimise the new artefact configuration states to generate higher forms of market value. | ||
| + | # Further design module artefact states are freely made available. | ||
| + | |||
| + | [[File:Artefact-opennes-state-flow-PLC-&-end-users.gif|400px|border]] | ||
| + | |||
| + | '''Figure 1. Artefact openness state within hacker innovation activities. Artefacts are made open by hackers at the ‘hack point’ allowing for new artefact configuration states to exist in the pursuit of higher value.''' | ||
| + | |||
| + | In the case of the Android smartphone market, the state of artefact openness occurs by the following states: | ||
| + | |||
| + | # Open (core Linux kernel) | ||
| + | # Open (Android software layer) | ||
| + | # Closed (proprietary firm shell layers added) | ||
| + | # Closed (product delivered to consumers) | ||
| + | # Open (hackers re-open artefact states to allow for further innovations) | ||
| + | |||
| + | === Consequences of open code in consumer products === | ||
| + | |||
| + | As more and more consumer products depend upon embedded open code platforms such as Linux, there will most likely be a rise in the number of hacker innovations occurring to them. Hacker ethics, spirit and incentives, combine to create free data and information in the sense that it is free from ownership and used to pursue yet higher forms of value and functionality through exploration and experimentation of optimal artefact configuration states. The end goal for hackers is to fully optimise a technology for its intended and unintended use in executing tasks. | ||
| + | |||
| + | Firms prepared to learn and deeply understand, manage and leverage hacker innovation occurring to their product classes in distributed networks should be in a position to better meet wider consumer needs by absorbing new knowledge from continually developing and optimised module configuration states throughout a products lifecycle. Flowers [Flowers, 2006] discussed a framework detailing potential firm responses to hacker innovation, but primary research is yet to reveal empirical evidence on how different strategies are being employed by incumbents in a selection of product markets. | ||
| + | |||
| + | Knowledge in hacker communities is distributed among network actors, forming in similar ways to ad-hoc film production teams as project networks [Sydow and Staber, 2002]. Self-organising, self-governing collaborative teams form into loose and fluid organisational forms to pursue and complete creative hacker projects. Members freely decide to form, leave and contribute to development teams as they wish, without the direction of any upper management. Despite this, complete and detailed records of actor communications, module configurations and changes are publicly available held in MySQL database records held in online forum databases for potential primary data analyses. | ||
| + | |||
| + | This discussion will move on to some real world examples of collaborative hacker innovation outputs by communities and individuals where firms have directly opposed and fought outputs in an attempt to protect vested interests and intellectual property as well as those who have sought to leverage hacker outputs to help build further forms of competitive advantage. | ||
| + | |||
| + | === Case Study: Sony PlayStation 3 hacking responses and consequences of closing-out hacker innovation entirely === | ||
| + | |||
| + | Sony has a long history of aggressively and confrontationally combating forms of hacker innovation occurring to its product portfolio.<ref>Further reading of such cases: ‘Sony’s War on Makers, Hackers & Innovators’ http://blog.makezine.com/2011/02/24/sonys-war-on-makers-hackers-and-innovators/</ref> One such case occurred in 2010 and resulted in hundreds of millions of dollars worth of damages to Sony including the largest hacktivist data theft seen to date, with the theft of an estimated 77 million user accounts. The stakes are clearly high for firms who adopt an attack approach to hackers, relying upon litigation and legal structures designed to combat intra-firm IP infringements, rather than fighting against valued users and end consumers that the firm relies upon for its future continued growth. | ||
| + | |||
| + | In January 2010 a 15-year-old American named George Hotz (known as ''GeoHot'') announced he had hacked the Sony’s original firmware and created a custom version that allowed read and write access to the console’s system and processor. This enabled him and others to install a version of Linux to run on the PlayStation 3 (PS3). Sony responded in March by releasing a console firmware update that removed the ‘''Other OS''’ from the system boot menu, a feature that had previously allowed booting into a Linux distribution such as Ubuntu, Yellow Dog Linux, Open SUSE or Fedora using Hotz’s exploit. Sony instantly, without warning shut out the entire worldwide hacker community in one update patch. | ||
| + | |||
| + | In response to this, in the following January Hotz hacked, announced and published Sony’s much guarded root keys (permitting the system to run any customised code and unpreventable by Sony simply releasing a future firmware patch, without installing new hardware altogether). This resulted in a class action lawsuit by Sony against Hotz claiming: | ||
| + | |||
| + | # Violation of the DMCA, CFAA, Copyright law, and California's CCDAFA | ||
| + | # Breach of Contract (related to the PlayStation Network User Agreement) | ||
| + | # Tortious interference, Misappropriation, and Tresspass.<ref>Sony’s full class action lawsuit against Hotz detailed at: http://www.archive.org/download/gov.uscourts.cand.226894/gov.uscourts.cand.226894.1.0.pdf</ref> | ||
| + | |||
| + | Further aggressive ''attack'' tactics by Sony included legal action to obtain the personal IP addresses from private logs of all those who had visited and viewed Hotz’ Twitter and personal Web site as well as those who had seen his rap video posted on YouTube about the ‘disaster’ of Sony in order to bring individual legal lawsuits against those who had merely viewed the hacker generated content, irrespective as to whether it was used for hacking or not.<ref>GeoHot’s rap video to Sony about his upcoming lawsuit: ‘The Light It Up Contest -- geohot,” available to view at: http://www.youtube.com/watch?v=9iUvuaChDEg.</ref> Such heavy-handed tactics severely angered many in the homebrew developer and hacker communities who felt that Sony’s actions deeply infringed upon common its ethics, freedom of information and openness and were deemed deeply unacceptable. Based upon these ethics, Hotz argued that people who legitimately purchase consumer devices should be allowed to modify them in any way they see fit. In response to the case, retaliations from renowned black hat security hacktivists Anonymous soon got underway against Sony after Hotz’s arrest, first occurring in April 2011 where groups hacked into the Sony network and steal over 77 million PlayStation user accounts, forcing Sony to shut down their entire gaming network 24 days, resulting in an estimated $150 million worth of damages. | ||
| + | |||
| + | The case highlighted the potential and actual consequences of taking an aggressive stance against hacker innovation groups and activities, resulting in enormous financial losses and immeasurable damage to firm image and identity. | ||
| + | |||
| + | [[File:Hackability-&-Firm-Boundaries.gif|400px|border]] | ||
| + | |||
| + | '''Product innovation hackability vs. degree of firm boundary openness.''' | ||
| + | |||
| + | Firms who develop technological artefacts with a high degree of hackability potential should take care in executing strategies that do not aggressively prevent hackers from exploring underlying systems modularity and further optimised design configurations within proprietary devices; whilst crucially at the same time protecting intellectual property in such a way as to permit legitimate rent appropriation. Firms that develop products and services with a high degree of hackability but closed firm boundaries are in a position to most highly benefit (or fail) if inappropriate and aggressive strategies are adopted. It would seem wise for firms to engage with hacker communities in the R&D phase of future product developments in order to create technological artefacts that engage with hacker users desires as well as meet broader user requirements in an attempt to reduce future negative ramifications and maintain market stability (Figure 1, above). | ||
| + | |||
| + | === XDA Developers smartphone and tablet hacking === | ||
| + | |||
| + | XDA Developers is a hacker innovation community currently comprising around 4.5 million members who continually hack and develop proprietary and Open Source smartphone software on various manufacturer platforms. One hundred and thirty nine devices are currently under development including smartphones, PDA’s, tablets and media streaming devices on Android, Windows Phone, WebOS, iOS and Bada operating systems. Hacker innovation is undertaken by fluid, self-organising teams of developers, testers and users. Groups are organised into project networks around each device and knowledge is freely distributed across teams based underpinned by underlying hacker ethics. | ||
| + | |||
| + | Hacker teams operating in a semi-competing manner, collaboratively in groups led by experienced software, firmware or read only memory (ROM) developers and operate similarly to internal innovation skunk works, somewhere in between a cathedral and a bazaar [Raymond, 2000]. Primary core hacker team members work in close collaboration with trusted partners to develop core systems based on personal design specifications, preference and performance requirements. Further secondary hackers develop customised individual sub- modules based on releases by the core team. Tertiary hackers simply install and use hacked system code by testing and reporting critical interdependencies, bugs and criticisms back to the primary hacker development team in order to rectify bugs in rapid incremental iterations, followed by new module configuration releases and versions. | ||
| + | |||
| + | Working in this way, all code is regarded as open and free of ownership. Propriety and open code found within complex module configurations like those found in the Android operating system are treated as one and the same thing with little regard for the boundaries and implications of modifying IP built on top of core open code projects augmented by proprietary closed code generated by firms. The Open Source model is applied to these artefacts whilst obtaining access by any means possible to allow for modifications to be made in spite of restrictions put in place by manufacturers. Development teams function in similar ways to the academic peer review model. Projects ROM’s (Read Only Memory operating systems such as Android) or small mods are released openly to the community for evaluation, testing, criticism. XDA functions as a system of development and improvement; or as sociologist Robert Merton coined, ‘organised scepticism’. | ||
| + | |||
| + | '''How the XDA open development model works:''' | ||
| + | |||
| + | #An individual finds a problem or goal that is personally significant with an existing technology. | ||
| + | # Barriers to innovation are removed by hacking device bootloaders. | ||
| + | # A software solution is released to the community and users freely install, test and develop a proposed solution. | ||
| + | # New additions, modification and changes are made to source code are passed on and contributors credited accordingly. | ||
| + | #New code is released based upon optimised module configuration results. | ||
| + | # Future code releases and innovation cycles are contingent upon innovation outputs by firms. | ||
| + | |||
| + | Innovation cycles occur efficiently and frequently in these ROM development teams and progress is made very quickly to resolve bugs and solve problems in the pursuit of artefact optimality. Many smartphone handset product reviews are now made using XDA developed ROM’s as they are regarded as vastly improved upon manufacturer efforts and reflect the true performance potential of devices. | ||
| + | |||
| + | Various legal cases have been brought against XDA such as the 2007 lawsuit where Microsoft asked XDA to remove all ROM’s that were developed on top of its propriety code by hacker community members. XDA responded with a 10,000-member petition against Microsoft’s demands who later dropped action against XDA’s hackers [Dennis, 2007]. A case such as this highlights the legislative grey area for firms and hackers alike. On the one hand IP infringements do occur, not by other competing firms, but by the firm’s valued customers. Microsoft’s stance was to quietly ignore hacking of its operating system for fear of alienating consumers, especially when the majority of hacked code developed to its ROM’s primarily runs on the very same handsets as originally intended by manufacturers. | ||
| + | |||
| + | '''Need for authoritarian structures in Open Source and hacker communities ''' | ||
| + | |||
| + | While generally opposed to hierarchy and bureaucracy, hacker communities depend upon lead figures such as Linus Torvalds from the Linux community. Torvalds directs the entire project, deciding which direction to take, what to include and exclude and what should be submitted to referee groups for peer review. | ||
| + | |||
| + | XDA development teams also function under the direction of a lead developer who commences projects, decides which modules to include and exclude and makes individual customisations and tweaks accordingly. Lead developers hack open and closed code, dissecting and discovering new optimisations through trial and error, modifying as they see fit. Performance, functionality and features are improved upon and finished ROM’s are distributed to other hackers to learn and develop from and to make further changes, improvements and advances.<ref>In some cases hacking software module configurations can result in varying overall quality in terms of functionality, stability, performance and design. Quality control and maintenance of common standards can result in a configuration that is entirely unfit for general purpose dependent upon end-user requirements, but none the less may be of little functional everyday use in mass markets.</ref> The XDA hacker community comprises an: | ||
| + | |||
| + | <blockquote>...online meritocracy in which [members have] bootstrapped themselves into surrogate families [who] learn together by trial and error, becoming a model of self-directed networked learning. They create a large-scale interactive system, self-regulating and self-organizing, flexible, adaptive, and unpredictable [Thieme, 2003].</blockquote> | ||
| + | |||
| + | The goal of the overall labour effort is to explore technology and to increase the ability of artefacts to function more flexibly in ways more highly optimal for each project goal while maintaining stability at high performance speed for the majority end users. XDA innovation occurs in distributed teams around the world via the use of digital innovation and communication technologies. Individuals self-assemble and self govern online whilst sharing a common set of cultural hacker ethics (openness, freedom and sharing of information) in the pursuit common desired goals: to reconfiguring existing technologies to better and higher capabilities and functions. This is achieved by recombining technologies in new ways to execute previously unimagined tasks. Hackers in this sense aim to better understand how a technology works by reverse engineering it and gaining new knowledge through use in order to explore how to best modify and improve it. | ||
| + | |||
| + | XDA hackers closely follow the seven values of protestant ethics: work, money, optimality, flexibility, stability, determinacy and accountability, including hacker values: passion, joy, intrinsic interest, freedom of information and creative play. Peer recognition, altruism and expected future returns are strong drivers for participation in Open Source project rather than for capital gains per se (Hars, 2001). Such motivations also exist within hacker communities like XDA developers, but do not provide the primary driver for participation. Evidence for this can be seen by public profiles displaying the number of posts made, ‘thanks’ received by other members, number of monetary donations made and experience level. Some hackers who regularly contribute to projects display a link to payment gateways whereby donations can be made by users who consider time expended by developers worthy enough to ‘buy them a beer’ as is informally known. Hackers who work on multiple devices at one time could potentially generate sufficient income from broad range of peer donations, to significantly supplement or outright negate the need for other sources of personal income. | ||
| + | |||
| + | === Case study: Wii Hacking and the Dolphin Emulator === | ||
| + | |||
| + | The Nintendo Wii games console is another example of hacker innovation spanning both extremes along the illegal-to-illegal dimension. Hacking a console involves finding ways to creatively circumvent firm implemented copy protection and code-signing measures to enable customised software to run outside of the control and intended use by manufacturers. Also known as ‘homebrew,’ Wii hacking spans the installation of physical hardware ‘mod chips’ to software modifications allowing for circumvention of manufacturer restrictions; and in the process severely infringes upon consumer license and EULA agreements, similar to the PS3 hacking case. | ||
| + | |||
| + | Hacking the Wii not only involves modifications to the console itself, but also to the development of emulators to enable the running of unsigned code on other platforms entirely.<ref>Less than a month after initial launch on November 18th 2012, the Nintendo Wii U (successor to the Wii) was hacked open allowing the new console to run the Homebrew Channel. This enabled customized firmware, pirate software and custom content to be executed. Nintendo will most likely release a future update to lock out the hack, forcing hackers to seek out other yet further exploits in a continual cyclical circumvention effort by both firm and end user. HackMii ‘HBC release for a new Wii U’ available at: http://hackmii.com/2012/12/hbc-release-for-a-new-wii-u, retrieved 10th December 2012.</ref> The Dolphin Emulator is an Open Source project that runs on PC, Mac and Linux platforms permitting Wii and GameCube software to be played on a desktops or laptops without using the need to use Nintendo’s console hardware at all or even the official game controllers. During initial diffusion the Wii received much criticism for the low resolution output capabilities of the console’s graphics card, particularly in light of new high resolution LCD flat screen TVs emerging in the marketplace at the time. In response to this, hackers developed the Dolphin Emulator with the added features and functionality that were not available from the manufacturer innovation including high definition 3D graphics amongst other features. Dolphin Emulator has been critically acclaimed as surpassing the innovation limits of the original console.<ref>More information about Dolphin Emulator: http://dolphin-emulator.com.</ref> | ||
| + | |||
| + | Consequences of such a project include a potential increase in games piracy and hardware component redundancy (in order to play games) as well as increase in the generativity output of new and emergent module configurations. The games console market business model is based upon accepting a loss on the sale of the hardware component and appropriating rents from licensing software rights to games developers. The more significant bottom line financial impact would most likely be felt by a reduction in consumer purchases of software made freely available instead through peer-to-peer file sharing networks; however other hardware components and peripherals would still be required in order to play games. All of the above consequences point towards a market driven design trajectory demonstrated by the augmenting and reconfiguring of the original innovation’s features: | ||
| + | |||
| + | * High Definition graphics engine | ||
| + | * Anti aliasing, anisotropic filtering | ||
| + | * Post processing pixel shading | ||
| + | * Hardware accelerated texture processing | ||
| + | * Widescreen support | ||
| + | * 3D capabilities | ||
| + | * Cross platform functionality | ||
| + | * Action replays | ||
| + | * Multi controller support (tablets, tablets, other games console controller | ||
| + | support) | ||
| + | * Support for homebrew games | ||
| + | * Support for other operating systems | ||
| + | |||
| + | In effect hackers took a closed product, made it open and set about creating innovative features that the manufacturer had not implemented or foreseen in the research, development, design and manufacture of the final product. New artefact states have been generated to more closely meet the needs and desires of a segment of the lead user market through the removal of copyright restrictions, walled gardens and closed systems to permit creative exploration of the innovative potential held within tightly locked artefact module configurations and freely distributed (not for profit) under the Open Source license agreement. The end result is a manufacturer-developed technology, made into its own disruptor within the marketplace as the business model starts to fail when rent appropriation channels are broken down by acts of hacking (hence legal action responses). The hacker innovation labour efforts made indicate critical market driven design trajectories that can be foreseen for future product generations allowing for valuable design lessons to be absorbed and implemented in later products. | ||
| + | |||
| + | NEXT: '''Chapter 5.2''' - [[Product Innovations Designed to be Hacked]] | ||
| + | |||
| + | <disqus></disqus> | ||
| + | |||
| + | |||
| + | [[File:hackers-and-innovation-epub-pdf-book111.png|250px|link=http://www.mikepinder.co.uk/store/e-books/hackers-innovation-redefinition-examination-outlaw-sources-generativity-future-product-development-strategies/ ]] | ||
| + | |||
| + | <big>'''''Purchase E-Book (ePub & PDF) Version'''''</big> | ||
| + | |||
| + | You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader. | ||
| + | |||
| + | [[File:add-basket-version.png|link=http://www.mikepinder.co.uk/store/e-books/hackers-innovation-redefinition-examination-outlaw-sources-generativity-future-product-development-strategies/]] | ||
| Line 82: | Line 204: | ||
* [*Telecom, 2012] Telecom, S. a. S. (2012). Android Smartphone Activations Reached 331 Million in Q1 2012. | * [*Telecom, 2012] Telecom, S. a. S. (2012). Android Smartphone Activations Reached 331 Million in Q1 2012. | ||
* [*Baldwin, 2000] Baldwin, C. C., B. (2000). Design Rules Volume 1. The Power of Modularity. Cambridge, Massachusetts, The MIT Press. | * [*Baldwin, 2000] Baldwin, C. C., B. (2000). Design Rules Volume 1. The Power of Modularity. Cambridge, Massachusetts, The MIT Press. | ||
| − | * [* | + | * [*Sydow and Staber, 2002] Sydow, J. and U. Staber (2002). "The Institutional Embeddedness of Project Networks: The Case of Content Production in German Television." Regional Studies 36(3): 215-227. |
| − | * [* | + | * [*Flowers, 2006] Flowers, S. (2006). KNOWLEDGE, INNOVATION AND COMPETITIVENESS: DYNAMICS OF FIRMS, NETWORKS, REGIONS AND INSTITUTIONS. DRUID Summer Conference 2006. Denmark. |
| + | * [*Raymond, 2000] Raymond, E. S. (2000). "The Cathedral and the Bazaar." from http://www.tuxedo.org/~esr/. | ||
| + | * [*Dennis, 2007] Dennis, T. (2007). "Microsoft stomps on XDA developers." Retrieved Sep, 2012, from http://www.theinquirer.net/inquirer/news/1018935/microsoft-stomps-xda-developers. | ||
| + | * [*Thieme, 2003] Thieme, R. (2003). "Hacker Generations." Retrieved Sep, 2012, from http://www.ctheory.net/articles.aspx?id=394 | ||
| + | * [*Flowers, 2006] Flowers, S. (2006). KNOWLEDGE, INNOVATION AND COMPETITIVENESS: DYNAMICS OF FIRMS, NETWORKS, REGIONS AND INSTITUTIONS. DRUID Summer Conference 2006. Denmark. | ||
</HarvardReferences> | </HarvardReferences> | ||
Latest revision as of 10:42, 25 April 2016
Contents
- 1 Hacking consumer artefacts
- 2 Meaning change and swings of the pendulum
- 2.1 The original consumer hacker innovators: moonshine runners
- 2.2 Nerf Sports Toys
- 2.3 Key moment in consumer goods: open code hits the mainstream marketplace
- 2.4 Manufacturer and hacker artefact configuration states
- 2.5 Consequences of open code in consumer products
- 2.6 Case Study: Sony PlayStation 3 hacking responses and consequences of closing-out hacker innovation entirely
- 2.7 XDA Developers smartphone and tablet hacking
- 2.8 Case study: Wii Hacking and the Dolphin Emulator
- 3 Footnotes
- 4 References
Hacking consumer artefacts
Hackers believe one can learn “essential lessons about systems [and] about the World by taking things apart, seeing how they work, and using this knowledge to create new and more interesting things” [Levy, 1984]. When a hacker is faced with a closed and locked-down artefact this cannot happen so easily, if at all, and merely prevents the ability to act in a hands-on approach to a technology and access its potential state of being open and modifiable. In so doing hackers adopt a sense of what is defined as wilful blindness in pursuit of their passions and interests. More concretely, this means circumventing manufacturer access restrictions (device encryptions, boot-loaders, copy protection and rights management) resulting in breaches of end user license agreements (EULAs), copyright, trademark, intellectual property and patent law. Ironically the more a device is protected, locked and secured against hacking, the higher the chance of motivation by hacker-innovators to employ their skills to circumvent and gain higher meritocratic status within the community by doing so. George Hotz, hacker of the Sony PlayStation 3, who published the console’s core root access keys on his Twitter account, demonstrated this. His ‘criminal acts’ according to Sony, did not in any way harm his career prospects, going on to an unknown work position at Facebook.
Hacking of consumer artefacts can be split into various didactic dimensions dependent upon one’s moral, ethical, political and legal viewpoints:
- Illegal to legal
- Immoral to moral
- Destructive to constructive
- Value creation to value destruction
- Ethical to unethical
- Degenerative to generative
- Destroy to creating
- Stealing to sharing
- Contributing to taking
- Learning to using
Firms who create and depend upon the appropriation of rents from their intellectual property tend to adopt a critical view of hacking whilst keen to protect their vested interests within the market built on proprietary IP. Those who benefit from unrestricted exploration and optimisation of technologies adopt a beneficial, positive, useful and in some case essential view of hacking activities.
Meaning change and swings of the pendulum
Over time the meaning of a hacker has swung between the positive to negative dimensions as we have seen. Originating in the positive sense, as someone tinkering in a clever and previously unthought-of of way (woodwork, carpentry and craftsmanship), to the negative, with the emergence of the World Wide Web and computer criminals. Within the Open Source communities it has become a complimentary badge or term for a brilliant programmer; but in exploration of consumer artefacts it has swung back towards negativity (even in some cases if such consumer devices actually depend upon openly developed code, critical and fundamental to their function and operation). In TV, music, film and software it has come to reflect illegally pirated and distributed intellectual property, whether through bootlegging or creative mash-ups of other artist’s and labels work.
The problem with the general and popular usage of the hacker term in various forms is that it describes a common set of knowledge and skills that can be used for very different purposes, at both the positive and negative ends of the legal to illegal hacker dimension. The critical difference described so far is that of the intent of such hacker acts. At the negative and non-generative end, the intent is to steal, subvert, corrupt and destroy value; whilst at the more positive end, the intent is to generate value and societal usefulness by collaborating, sharing and cooperating in networks that optimise the functionality of artefacts through the unrestricted exploration of higher value design configuration states.
The original consumer hacker innovators: moonshine runners
With the emergence of consumerism in the early 20th Century (during the economic focus on the production of capital goods), a group of product hackers or bootleggers began to develop innovations that could allow for the unhindered distribution of illegal alcohol or ‘moonshine’ around the United States during Prohibition. These product hackers purchased small consumer standard specification cars and heavily modified or hacked them to improve speed, storage and handling capabilities in order to outrun law enforcement authorities and distribute illegal alcohol. When Prohibition ended in 1933, much of the illicit trade ceased, but innovation upon the cars continued and evolved into regularly organised race meets for prize money and profit, later to become the second most watched sport in the USA, second only to the National Football League (NFL) with an estimated 75 million fans.[1]
What made early NASCAR innovations attributable to the hacker mind-set were that significant modifications were made to existing (internally developed) technologies of the time that did not perform to the high standards requirements of the market’s lead consumers. As the sport matured and became legitimised by evolving into NASCAR, product hacking continued and provided the industry with a complimentary external R&D innovation source that has directly influenced the design trajectory of the entire consumer automotive industry as a whole. Some examples of these racing-bred hacker innovations include:
Manual transmission to allow racers to control the power to the wheels.
- Direct-shift gearboxes to allow gear changes quickly.
- Ignition keys on the right side (right hand drive) or left side (left hand drive) of car dashboards to allow simultaneous ignition and gear selection.
- Suspension design during cornering.
- Longevity of tyre rubber compounds.
- Disk brake development.
- Engine air intake and supercharger modifications.
- Dual Overhead Cam (DOHC) engines allowing for fuel and air valves to be open and shut more efficiently.
- Exterior design to make the most efficient and aerodynamic shapes.
- New materials development (carbon fibre, ceramics etc.) to make cars lighter and more efficient.
- Safety improvements (roll cages and rear view mirrors).
The NASCAR origins example demonstrates the influence and importance of hacker innovation upon the later evolution of the wider industry. Examples discussed later in this paper reflect the same phenomena with an important difference: hacker innovation occurs to existing technologies, but is largely dismissed or ignored by firms entirely (despite the potential importance and wider significance these activities may have on future design trajectories). Perhaps falling foul of the Not Invented Here Syndrome and demonstrating a lack of absorptive capacity [Katz and Allen, 1982] [Cohen and Levinthal, 1990].
Nerf Sports Toys
Hacker innovation can originate externally from users of all ages but in some cases may not be suitable for reabsorption by the firm. One such example is Nerf, a children’s toy manufacturer of foam-based weapons that fire foam based projectiles to around 60 feet. Children’s toy guns must meet strict US safety regulations in order to enter products into the market, so child hackers developing blaster mods directly challenge the company’s safety-based marketing messages. As such all forms of modding are in no way endorsed by Nerf. Hacker innovators do not have to meet such safety regulations at home and a vast array of ‘Nerf mods’ are available in online community Web sites. Both the firm and the consumer have an innovation desire to design weapons that can fire foam projectiles as far as technically possible. The difference being hacker consumers are free to modify as the see fit and firms are strictly controlled.
Hacker mods include removing air restrictors, sealing air releases, lengthening barrels from Crayola Washable Markers, homebrew darts and recombining models in new configurations. All mods are designed to increase the artefact performance through the use of the same design module operators as discussed in computer programming context; but the crucial difference being these particular resultant hacks are not legally admissible by the firm for reabsorption. Where health and safety considerations do not pose barrier issues to firms, then resultant hacks may be suitable for firms to listen, learn, absorb innovations from external hackers to develop and alter future design trajectories within product classes.
Key moment in consumer goods: open code hits the mainstream marketplace
The industry life cycle model of Open Source software development has surpassed the initial introduction and growth phases and is entering the mature stage of its development [Rogers, 1995]. This occurred after the purchase of Android Inc., by Google in 2005. Linux at this point became embedded for the first time in a true mass-market consumer product: the smartphone. By the end of 2012, 400 million Android handsets were in use with over 1,000,000 devices activated every day at an estimated 54% market share [Telecom, 2012]. Never before has an Open Source software platform been so extensively diffused and adopted in the hands of everyday consumers as a truly dominant mass-market product based almost entirely upon openly developed code in direct competition to internally developed proprietary offerings.[2]
Up until this point previous variants of the Linux kernel and operating system had been deployed mainly in infrastructure environments, desktop computers, Web servers and mainframes, industrial automation and medical instruments to name a few. But in more recent years (due to its low cost and ease of portability), Linux has been deployed in more and more consumer electronic devices such as routers, set-top boxes, televisions, games consoles, media players, tablets and desktop computers. Such embedded Linux devices incur little or no royalty or licensing fees to other firms under the GPL license and can be modified, ported and redistributed along with underlying source code to other platforms and devices remarkably easily and quickly compared to closed development, proprietary code.
As well as smartphones, Android is being deployed in a variety of other consumer devices such as laptops, netbooks, wristwatches, headphones, car audio players, tablet computers, headphones, digital cameras and portable music players. The list is constantly growing. The result has been a relatively fast spread in the application of common, openly developed knowledge within the consumer marketplace. The tools and means for developing and improving mass produced artefacts is being democratised, allowing for development contributions made to existing technologies from many different sources, amplified by the use of the Linux kernel at the core and its availability of surrounding knowledge. Hacking opens up devices to further modifications, regardless of firm efforts in attempting to lock out unauthorised access. As the Linux kernel is developed within a vastly distributed Open Source ecosystem comprising contributors and developers from all over the World, there is a vast audience of consumers with directly applicable knowledge and experience in developing and modifying the software for employment as well as hobbyist, passionate activities.
The Linux Foundation recently reported statistics demonstrating the extent of Linux adoption by firms in consumer electronic devices (Foundation, 2012). Statistics reveal that 700,000 televisions and 850,000 Android mobile phones are sold with Linux every day. Since 2005, 800 developers in 800 companies were contributing to the Linux kernel, which now consists of 15 million lines of code, with development cycles every two to three months (compared to two or three years for proprietary operating systems).
Combined with hacker ethics, code originating in the Open Source model with proprietary software module layers developed by firms in the product development process (closing-off external access to hybrid code), also ends up being hacked open again by hacker groups. The result is a hotbed of divergent interests, copyright infringements, uncontrollable and unregulated design evolution trajectories developed in various distributed organisational forms diffused through interconnected digital technologies. In short, hackers further contribute to industry fragmentation based upon an openly developed platform in the aftermarket after initial consumption.
As the demand for multifunction devices (telephony, mp3 and media players, gaming, photo and video cameras) increases with progress and complexity, Linux offers a pre-packaged suite of multi-threaded software capable of modular adaptation to ever more complex environments with free source code, no license fees and no unit royalties [Baldwin, 2000]. Use of Linux reduces internal R&D and time to market, but also causes product differentiation problems with other product manufacturers in the same markets. Manufacturers are forced to differentiate on top of the core platform by adding proprietary software shell layers and when hackers open up the devices to modifications they immediately tread on murky legal waters in terms of handling, modifying and using proprietary code.
The first foray for Linux into the mass consumer electronic market came in 1999 with TiVo Inc. by launching a new Linux based personal digital video recorder (DVR), allowing for a plethora of new features and functionality over the extant cassette tape video recorders with features such as pausing live TV, selecting programmes based on personalised interests and skipping advertisements in recordings. One crucial feature was the ability to connect to user’s home network and Internet connection to receive and download online scheduling information and service updates. The networking functionality allowed a way in and means for hackers to write programs and execute code within the system itself in ways unintended or even possibly imagined by TiVo Inc. themselves.
Both Computer Hobbyist and Enthusiast Programmer hacker types worked in collaborative innovation networks sharing knowledge via online technologies in to hack the TiVo box to enable service improvements such as circumventing country and regional blocks, installing larger hard drives, extracting videos to other PC’s and other TiVo boxes as well as file format decoding and encoding restriction removals. Essentially these hacks were carried out not to steal data, commit crime, destroy property or for personal financial gain, but were made to explore, unlock and share the unrealised potential functionality of design module configurations for personal benefit and as a passionate and pleasurable experience.
Manufacturer and hacker artefact configuration states
The work undertaken by firm and hacker environments results in different artefact states as new module configurations are created, diffused and adopted by both parties (see conceptual diagram in Figure 1 below). Here artefacts pass from: an open to closed to open again configuration state.
- A manufacturer develops a new product based upon Open Source code with propriety software modules incorporated at shell layers.
- Proprietary and open code enters the marketplace locked and held within software and hardware configurations.
- Where access restrictions are found, hackers re-open the artefact to enable exploration of more optimised and feature rich design configuration states (at the hack point).
- Hacker groups emerge through the use of ICT’s technologies sharing knowledge, learning and experience in order to optimise the new artefact configuration states to generate higher forms of market value.
- Further design module artefact states are freely made available.
Figure 1. Artefact openness state within hacker innovation activities. Artefacts are made open by hackers at the ‘hack point’ allowing for new artefact configuration states to exist in the pursuit of higher value.
In the case of the Android smartphone market, the state of artefact openness occurs by the following states:
- Open (core Linux kernel)
- Open (Android software layer)
- Closed (proprietary firm shell layers added)
- Closed (product delivered to consumers)
- Open (hackers re-open artefact states to allow for further innovations)
Consequences of open code in consumer products
As more and more consumer products depend upon embedded open code platforms such as Linux, there will most likely be a rise in the number of hacker innovations occurring to them. Hacker ethics, spirit and incentives, combine to create free data and information in the sense that it is free from ownership and used to pursue yet higher forms of value and functionality through exploration and experimentation of optimal artefact configuration states. The end goal for hackers is to fully optimise a technology for its intended and unintended use in executing tasks.
Firms prepared to learn and deeply understand, manage and leverage hacker innovation occurring to their product classes in distributed networks should be in a position to better meet wider consumer needs by absorbing new knowledge from continually developing and optimised module configuration states throughout a products lifecycle. Flowers [Flowers, 2006] discussed a framework detailing potential firm responses to hacker innovation, but primary research is yet to reveal empirical evidence on how different strategies are being employed by incumbents in a selection of product markets.
Knowledge in hacker communities is distributed among network actors, forming in similar ways to ad-hoc film production teams as project networks [Sydow and Staber, 2002]. Self-organising, self-governing collaborative teams form into loose and fluid organisational forms to pursue and complete creative hacker projects. Members freely decide to form, leave and contribute to development teams as they wish, without the direction of any upper management. Despite this, complete and detailed records of actor communications, module configurations and changes are publicly available held in MySQL database records held in online forum databases for potential primary data analyses.
This discussion will move on to some real world examples of collaborative hacker innovation outputs by communities and individuals where firms have directly opposed and fought outputs in an attempt to protect vested interests and intellectual property as well as those who have sought to leverage hacker outputs to help build further forms of competitive advantage.
Case Study: Sony PlayStation 3 hacking responses and consequences of closing-out hacker innovation entirely
Sony has a long history of aggressively and confrontationally combating forms of hacker innovation occurring to its product portfolio.[3] One such case occurred in 2010 and resulted in hundreds of millions of dollars worth of damages to Sony including the largest hacktivist data theft seen to date, with the theft of an estimated 77 million user accounts. The stakes are clearly high for firms who adopt an attack approach to hackers, relying upon litigation and legal structures designed to combat intra-firm IP infringements, rather than fighting against valued users and end consumers that the firm relies upon for its future continued growth.
In January 2010 a 15-year-old American named George Hotz (known as GeoHot) announced he had hacked the Sony’s original firmware and created a custom version that allowed read and write access to the console’s system and processor. This enabled him and others to install a version of Linux to run on the PlayStation 3 (PS3). Sony responded in March by releasing a console firmware update that removed the ‘Other OS’ from the system boot menu, a feature that had previously allowed booting into a Linux distribution such as Ubuntu, Yellow Dog Linux, Open SUSE or Fedora using Hotz’s exploit. Sony instantly, without warning shut out the entire worldwide hacker community in one update patch.
In response to this, in the following January Hotz hacked, announced and published Sony’s much guarded root keys (permitting the system to run any customised code and unpreventable by Sony simply releasing a future firmware patch, without installing new hardware altogether). This resulted in a class action lawsuit by Sony against Hotz claiming:
- Violation of the DMCA, CFAA, Copyright law, and California's CCDAFA
- Breach of Contract (related to the PlayStation Network User Agreement)
- Tortious interference, Misappropriation, and Tresspass.[4]
Further aggressive attack tactics by Sony included legal action to obtain the personal IP addresses from private logs of all those who had visited and viewed Hotz’ Twitter and personal Web site as well as those who had seen his rap video posted on YouTube about the ‘disaster’ of Sony in order to bring individual legal lawsuits against those who had merely viewed the hacker generated content, irrespective as to whether it was used for hacking or not.[5] Such heavy-handed tactics severely angered many in the homebrew developer and hacker communities who felt that Sony’s actions deeply infringed upon common its ethics, freedom of information and openness and were deemed deeply unacceptable. Based upon these ethics, Hotz argued that people who legitimately purchase consumer devices should be allowed to modify them in any way they see fit. In response to the case, retaliations from renowned black hat security hacktivists Anonymous soon got underway against Sony after Hotz’s arrest, first occurring in April 2011 where groups hacked into the Sony network and steal over 77 million PlayStation user accounts, forcing Sony to shut down their entire gaming network 24 days, resulting in an estimated $150 million worth of damages.
The case highlighted the potential and actual consequences of taking an aggressive stance against hacker innovation groups and activities, resulting in enormous financial losses and immeasurable damage to firm image and identity.
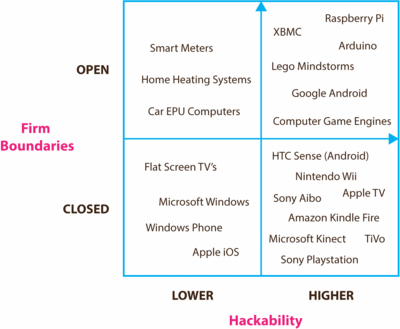
Product innovation hackability vs. degree of firm boundary openness.
Firms who develop technological artefacts with a high degree of hackability potential should take care in executing strategies that do not aggressively prevent hackers from exploring underlying systems modularity and further optimised design configurations within proprietary devices; whilst crucially at the same time protecting intellectual property in such a way as to permit legitimate rent appropriation. Firms that develop products and services with a high degree of hackability but closed firm boundaries are in a position to most highly benefit (or fail) if inappropriate and aggressive strategies are adopted. It would seem wise for firms to engage with hacker communities in the R&D phase of future product developments in order to create technological artefacts that engage with hacker users desires as well as meet broader user requirements in an attempt to reduce future negative ramifications and maintain market stability (Figure 1, above).
XDA Developers smartphone and tablet hacking
XDA Developers is a hacker innovation community currently comprising around 4.5 million members who continually hack and develop proprietary and Open Source smartphone software on various manufacturer platforms. One hundred and thirty nine devices are currently under development including smartphones, PDA’s, tablets and media streaming devices on Android, Windows Phone, WebOS, iOS and Bada operating systems. Hacker innovation is undertaken by fluid, self-organising teams of developers, testers and users. Groups are organised into project networks around each device and knowledge is freely distributed across teams based underpinned by underlying hacker ethics.
Hacker teams operating in a semi-competing manner, collaboratively in groups led by experienced software, firmware or read only memory (ROM) developers and operate similarly to internal innovation skunk works, somewhere in between a cathedral and a bazaar [Raymond, 2000]. Primary core hacker team members work in close collaboration with trusted partners to develop core systems based on personal design specifications, preference and performance requirements. Further secondary hackers develop customised individual sub- modules based on releases by the core team. Tertiary hackers simply install and use hacked system code by testing and reporting critical interdependencies, bugs and criticisms back to the primary hacker development team in order to rectify bugs in rapid incremental iterations, followed by new module configuration releases and versions.
Working in this way, all code is regarded as open and free of ownership. Propriety and open code found within complex module configurations like those found in the Android operating system are treated as one and the same thing with little regard for the boundaries and implications of modifying IP built on top of core open code projects augmented by proprietary closed code generated by firms. The Open Source model is applied to these artefacts whilst obtaining access by any means possible to allow for modifications to be made in spite of restrictions put in place by manufacturers. Development teams function in similar ways to the academic peer review model. Projects ROM’s (Read Only Memory operating systems such as Android) or small mods are released openly to the community for evaluation, testing, criticism. XDA functions as a system of development and improvement; or as sociologist Robert Merton coined, ‘organised scepticism’.
How the XDA open development model works:
- An individual finds a problem or goal that is personally significant with an existing technology.
- Barriers to innovation are removed by hacking device bootloaders.
- A software solution is released to the community and users freely install, test and develop a proposed solution.
- New additions, modification and changes are made to source code are passed on and contributors credited accordingly.
- New code is released based upon optimised module configuration results.
- Future code releases and innovation cycles are contingent upon innovation outputs by firms.
Innovation cycles occur efficiently and frequently in these ROM development teams and progress is made very quickly to resolve bugs and solve problems in the pursuit of artefact optimality. Many smartphone handset product reviews are now made using XDA developed ROM’s as they are regarded as vastly improved upon manufacturer efforts and reflect the true performance potential of devices.
Various legal cases have been brought against XDA such as the 2007 lawsuit where Microsoft asked XDA to remove all ROM’s that were developed on top of its propriety code by hacker community members. XDA responded with a 10,000-member petition against Microsoft’s demands who later dropped action against XDA’s hackers [Dennis, 2007]. A case such as this highlights the legislative grey area for firms and hackers alike. On the one hand IP infringements do occur, not by other competing firms, but by the firm’s valued customers. Microsoft’s stance was to quietly ignore hacking of its operating system for fear of alienating consumers, especially when the majority of hacked code developed to its ROM’s primarily runs on the very same handsets as originally intended by manufacturers.
Need for authoritarian structures in Open Source and hacker communities
While generally opposed to hierarchy and bureaucracy, hacker communities depend upon lead figures such as Linus Torvalds from the Linux community. Torvalds directs the entire project, deciding which direction to take, what to include and exclude and what should be submitted to referee groups for peer review.
XDA development teams also function under the direction of a lead developer who commences projects, decides which modules to include and exclude and makes individual customisations and tweaks accordingly. Lead developers hack open and closed code, dissecting and discovering new optimisations through trial and error, modifying as they see fit. Performance, functionality and features are improved upon and finished ROM’s are distributed to other hackers to learn and develop from and to make further changes, improvements and advances.[6] The XDA hacker community comprises an:
...online meritocracy in which [members have] bootstrapped themselves into surrogate families [who] learn together by trial and error, becoming a model of self-directed networked learning. They create a large-scale interactive system, self-regulating and self-organizing, flexible, adaptive, and unpredictable [Thieme, 2003].
The goal of the overall labour effort is to explore technology and to increase the ability of artefacts to function more flexibly in ways more highly optimal for each project goal while maintaining stability at high performance speed for the majority end users. XDA innovation occurs in distributed teams around the world via the use of digital innovation and communication technologies. Individuals self-assemble and self govern online whilst sharing a common set of cultural hacker ethics (openness, freedom and sharing of information) in the pursuit common desired goals: to reconfiguring existing technologies to better and higher capabilities and functions. This is achieved by recombining technologies in new ways to execute previously unimagined tasks. Hackers in this sense aim to better understand how a technology works by reverse engineering it and gaining new knowledge through use in order to explore how to best modify and improve it.
XDA hackers closely follow the seven values of protestant ethics: work, money, optimality, flexibility, stability, determinacy and accountability, including hacker values: passion, joy, intrinsic interest, freedom of information and creative play. Peer recognition, altruism and expected future returns are strong drivers for participation in Open Source project rather than for capital gains per se (Hars, 2001). Such motivations also exist within hacker communities like XDA developers, but do not provide the primary driver for participation. Evidence for this can be seen by public profiles displaying the number of posts made, ‘thanks’ received by other members, number of monetary donations made and experience level. Some hackers who regularly contribute to projects display a link to payment gateways whereby donations can be made by users who consider time expended by developers worthy enough to ‘buy them a beer’ as is informally known. Hackers who work on multiple devices at one time could potentially generate sufficient income from broad range of peer donations, to significantly supplement or outright negate the need for other sources of personal income.
Case study: Wii Hacking and the Dolphin Emulator
The Nintendo Wii games console is another example of hacker innovation spanning both extremes along the illegal-to-illegal dimension. Hacking a console involves finding ways to creatively circumvent firm implemented copy protection and code-signing measures to enable customised software to run outside of the control and intended use by manufacturers. Also known as ‘homebrew,’ Wii hacking spans the installation of physical hardware ‘mod chips’ to software modifications allowing for circumvention of manufacturer restrictions; and in the process severely infringes upon consumer license and EULA agreements, similar to the PS3 hacking case.
Hacking the Wii not only involves modifications to the console itself, but also to the development of emulators to enable the running of unsigned code on other platforms entirely.[7] The Dolphin Emulator is an Open Source project that runs on PC, Mac and Linux platforms permitting Wii and GameCube software to be played on a desktops or laptops without using the need to use Nintendo’s console hardware at all or even the official game controllers. During initial diffusion the Wii received much criticism for the low resolution output capabilities of the console’s graphics card, particularly in light of new high resolution LCD flat screen TVs emerging in the marketplace at the time. In response to this, hackers developed the Dolphin Emulator with the added features and functionality that were not available from the manufacturer innovation including high definition 3D graphics amongst other features. Dolphin Emulator has been critically acclaimed as surpassing the innovation limits of the original console.[8]
Consequences of such a project include a potential increase in games piracy and hardware component redundancy (in order to play games) as well as increase in the generativity output of new and emergent module configurations. The games console market business model is based upon accepting a loss on the sale of the hardware component and appropriating rents from licensing software rights to games developers. The more significant bottom line financial impact would most likely be felt by a reduction in consumer purchases of software made freely available instead through peer-to-peer file sharing networks; however other hardware components and peripherals would still be required in order to play games. All of the above consequences point towards a market driven design trajectory demonstrated by the augmenting and reconfiguring of the original innovation’s features:
- High Definition graphics engine
- Anti aliasing, anisotropic filtering
- Post processing pixel shading
- Hardware accelerated texture processing
- Widescreen support
- 3D capabilities
- Cross platform functionality
- Action replays
- Multi controller support (tablets, tablets, other games console controller
support)
- Support for homebrew games
- Support for other operating systems
In effect hackers took a closed product, made it open and set about creating innovative features that the manufacturer had not implemented or foreseen in the research, development, design and manufacture of the final product. New artefact states have been generated to more closely meet the needs and desires of a segment of the lead user market through the removal of copyright restrictions, walled gardens and closed systems to permit creative exploration of the innovative potential held within tightly locked artefact module configurations and freely distributed (not for profit) under the Open Source license agreement. The end result is a manufacturer-developed technology, made into its own disruptor within the marketplace as the business model starts to fail when rent appropriation channels are broken down by acts of hacking (hence legal action responses). The hacker innovation labour efforts made indicate critical market driven design trajectories that can be foreseen for future product generations allowing for valuable design lessons to be absorbed and implemented in later products.
NEXT: Chapter 5.2 - Product Innovations Designed to be Hacked
blog comments powered by DisqusPurchase E-Book (ePub & PDF) Version
You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader.
Footnotes
- ↑ According to the National Association for Stock Car Auto Racing Inc. (NASCAR): http://www.nascar.com/guides/about/
- ↑ Linux as a whole can be found in nearly all forms of digital technology including super computers, Web infrastructure, data centres, games consoles, mobile phones, media centres, mp3 players and many others. According to the Linux Foundation 700,000 televisions are sold with Linux every day and nine out of ten super computers in the World run Linux. Since 2005, eight hundred developers in eight hundred firms contributed to the kernel and 15 million lines of code have been coded with 1.5 million written in the past few years alone at a cycle rate of six module patches released every hour of every day. More information about Linux available at: http://www.linuxfoundation.org/
- ↑ Further reading of such cases: ‘Sony’s War on Makers, Hackers & Innovators’ http://blog.makezine.com/2011/02/24/sonys-war-on-makers-hackers-and-innovators/
- ↑ Sony’s full class action lawsuit against Hotz detailed at: http://www.archive.org/download/gov.uscourts.cand.226894/gov.uscourts.cand.226894.1.0.pdf
- ↑ GeoHot’s rap video to Sony about his upcoming lawsuit: ‘The Light It Up Contest -- geohot,” available to view at: http://www.youtube.com/watch?v=9iUvuaChDEg.
- ↑ In some cases hacking software module configurations can result in varying overall quality in terms of functionality, stability, performance and design. Quality control and maintenance of common standards can result in a configuration that is entirely unfit for general purpose dependent upon end-user requirements, but none the less may be of little functional everyday use in mass markets.
- ↑ Less than a month after initial launch on November 18th 2012, the Nintendo Wii U (successor to the Wii) was hacked open allowing the new console to run the Homebrew Channel. This enabled customized firmware, pirate software and custom content to be executed. Nintendo will most likely release a future update to lock out the hack, forcing hackers to seek out other yet further exploits in a continual cyclical circumvention effort by both firm and end user. HackMii ‘HBC release for a new Wii U’ available at: http://hackmii.com/2012/12/hbc-release-for-a-new-wii-u, retrieved 10th December 2012.
- ↑ More information about Dolphin Emulator: http://dolphin-emulator.com.
References
- [Levy, 1984] ^ Levy, S. (1984). Hackers: Heroes of the Computer Revolution, Penguin.
- [Katz and Allen, 1982] ^ Katz, R. and T. J. Allen (1982). "Investigating the Not Invented Here (NIH) syndrome: A look at the performance, tenure, and communication patterns of 50 R & D Project Groups." R&D Management 12(1): 7-20.
- [Cohen and Levinthal, 1990] ^ Cohen, W. M. and D. A. Levinthal (1990). "Absorptive Capacity: A New Perspective on Learning and Innovation." Administrative Science Quarterly(35): 182-152.
- [Rogers, 1995] ^ Rogers, E. M. (1995). Diffusion of Innovations. New York, The Free Press.
- [Telecom, 2012] ^ Telecom, S. a. S. (2012). Android Smartphone Activations Reached 331 Million in Q1 2012.
- [Baldwin, 2000] ^ Baldwin, C. C., B. (2000). Design Rules Volume 1. The Power of Modularity. Cambridge, Massachusetts, The MIT Press.
- [Sydow and Staber, 2002] ^ Sydow, J. and U. Staber (2002). "The Institutional Embeddedness of Project Networks: The Case of Content Production in German Television." Regional Studies 36(3): 215-227.
- [Flowers, 2006] ^ Flowers, S. (2006). KNOWLEDGE, INNOVATION AND COMPETITIVENESS: DYNAMICS OF FIRMS, NETWORKS, REGIONS AND INSTITUTIONS. DRUID Summer Conference 2006. Denmark.
- [Raymond, 2000] ^ Raymond, E. S. (2000). "The Cathedral and the Bazaar." from http://www.tuxedo.org/~esr/.
- [Dennis, 2007] ^ Dennis, T. (2007). "Microsoft stomps on XDA developers." Retrieved Sep, 2012, from http://www.theinquirer.net/inquirer/news/1018935/microsoft-stomps-xda-developers.
- [Thieme, 2003] ^ Thieme, R. (2003). "Hacker Generations." Retrieved Sep, 2012, from http://www.ctheory.net/articles.aspx?id=394
- [Flowers, 2006] ^ Flowers, S. (2006). KNOWLEDGE, INNOVATION AND COMPETITIVENESS: DYNAMICS OF FIRMS, NETWORKS, REGIONS AND INSTITUTIONS. DRUID Summer Conference 2006. Denmark.